Secure software supply chains are imperative to national security. When software supply chains come under attack, hackers and foreign adversaries compromise software to gain access to critical infrastructure, conduct espionage, and destroy information. As demonstrated by recent cyberattacks against SolarWinds and Microsoft Exchange, software supply chains are exposed and will continue to face assaults by nefarious actors unless the United States takes action to secure them.
A critical foundation of both public and private software supply chains is open source software (OSS). In fact, approximately 98% of codebases<fn-sp>1<fn-sp> contain OSS components.<fn-sp>2<fn-sp> However, OSS is substantially supported by software engineers working on a volunteer basis who do not always prioritize security, potentially endangering our crucial software supply chains.
The federal government can play a greater role in safeguarding software supply chains by securing open source development in two ways:
As Congress prepares the upcoming FY 2022 National Defense Authorization Act (NDAA), one way to accomplish these recommendations is to include the establishment of a Center for Open Source Software Infrastructure and Security.
Open source software is widely relied upon, but poorly supported, putting our national security at risk.
Like roads and bridges for the digital world, open source software (OSS) makes up much of our digital infrastructure and underlies many critical software systems, both public and private. Sometimes referred to as “free and open source software” (FOSS), OSS can be used, modified, and shared by the public according to its terms of distribution.<fn-sp>4<fn-sp>
OSS usage is widespread and especially common in the private sector due to the relative benefits of OSS compared to proprietary software, such as innovation and convenience. The OSS operating system Linux — which is available for anyone to use and contribute improvements — is utilized by nearly 40% of all web servers.<fn-sp>5<fn-sp>
The federal government has also been on the cutting edge of OSS technology. In fact, by 2003, OSS was so commonly used in the Department of Defense (DoD) that one study by MITRE — a nonprofit that manages federally funded research and development centers for several federal agencies — determined the software was “vital to DoD information security” for its reliability and quality.<fn-sp>6<fn-sp>
Since then, OSS usage has grown substantially. A recent survey by the software company Synopsys found that more than 98% of audited codebases contained open source components, and 75% of all code was open source — an increase from 36% in 2015.<fn-sp>7<fn-sp>
However, widespread adoption of OSS coincides with increased risks to software supply chain security. In 2014, the OSS library OpenSSL — a library maintained by volunteers that handles secure communications for 17% of servers across the Internet — disclosed the Heartbleed Bug, a vulnerability that exposed approximately 500,000 websites to exploitation.<fn-sp>8<fn-sp> In 2017, the consumer credit reporting agency Equifax announced a data breach caused by members of the Chinese People’s Liberation Army — exposing the personal information of 147 million people and leading to a USD 425 million settlement<fn-sp>9<fn-sp> — through a weakness in the OSS web hosting framework Apache Struts.<fn-sp>10<fn-sp> According to the Cybersecurity and Infrastructure Security Agency (CISA), two of the top ten routinely exploited information-technology vulnerabilities were related to OSS as of 2020.<fn-sp>11<fn-sp>
OSS-related vulnerabilities have become so acute that members of the House Energy and Commerce Committee raised the issue in a 2018 letter to the Linux Foundation, questioning the security and sustainability of the OSS ecosystem.<fn-sp>12<fn-sp> President Biden’s May 2021 Executive Order on Improving the Nation’s Cybersecurity also noted the importance of understanding the provenance of OSS in software supply chains.<fn-sp>13<fn-sp>
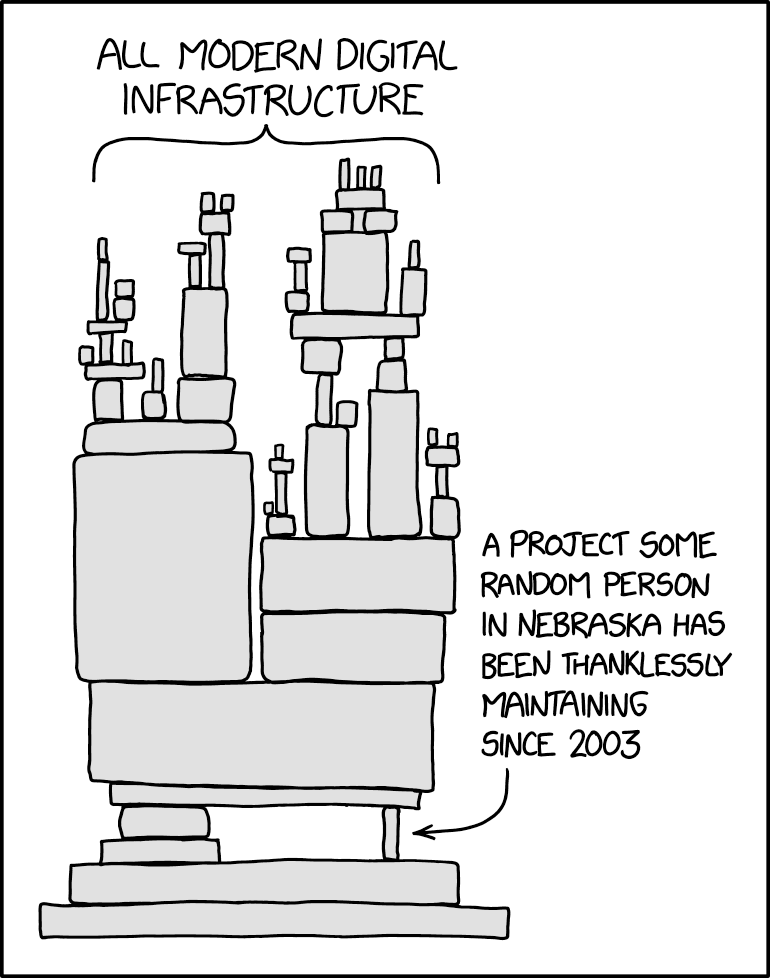
One of the primary reasons for these vulnerabilities is that OSS is often maintained by volunteers who do not always prioritize security, putting much of the Internet and millions of citizens at risk of attack. While some OSS projects are well-resourced by companies and non-profit organizations, other OSS code is maintained and released by people who struggle to monetize their work.<fn-sp>14<fn-sp>
According to a 2020 study by the Linux Foundation and the Laboratory for Innovation Science at Harvard, security fixes were among the external contributions that unpaid open source maintainers most desired, but among the areas where external contributors have the least interest to contribute. Maintainers would rather spend their volunteer time working on features or enhancements rather than security, which they described in terms such as “soul-withering chore.”<fn-sp>15<fn-sp> Moreover, 44% of open source maintainers surveyed in 2018 said that they have never conducted a security audit of their code.<fn-sp>16<fn-sp> The report concluded that “financial contributions to support FOSS development could be highly beneficial to increase their security and sustainability if primarily directed toward specific purposes.”<fn-sp>17<fn-sp>
When even closed source software developed by companies suffer supply chain attacks, such as the 2021 Microsoft Exchange attack and 2020 SolarWinds attack, it is all the more important to ensure open source has sufficient support. We wouldn’t rely solely on private companies and philanthropies to maintain and secure our roads and bridges that are open to the public; why would we do so for open source software?
The U.S. federal government must take action to better catalogue and fund the open source software ecosystem.
The United States needs to better secure its OSS supply chain at its source, or risk future attacks as OSS adoption increases and nefarious actors become more sophisticated.
The federal government can play a greater role in safeguarding software supply chains by securing open source development in two ways: 1) identifying and cataloging critical software in need of support, and 2) funding critical improvements in open source software security.
Congress should initiate an effort to systematically identify the most critical open source software components and develop criteria for determining the criticality and vulnerability of open source software. This effort can be coordinated with CISA, through the National Risk Management Center (NRMC), to determine the open source software components most important to the nation’s critical infrastructure sectors and National Critical Functions.<fn-sp>18<fn-sp> This effort should also engage NIST to determine guidelines for the criticality and vulnerability of open source software, creating criteria analogous to the Common Vulnerability Scoring System (CVSS).<fn-sp>19<fn-sp> The effort should result in an ongoing catalog that could be made available to other agencies as well as the public, analogous to the National Vulnerability Database (NVD) program.<fn-sp>20<fn-sp>
The effort for cataloging critical OSS could also build on existing work from (and involve collaborations with) related initiatives such as the Core Infrastructure Initiative’s Census Program<fn-sp>21<fn-sp> and the OpenSSF’s Criticality Score project.<fn-sp>22<fn-sp> Criteria for determining criticality and vulnerability could include: number of users of the OSS, code complexity of the system, number of full-time developers already working on the open source library, usage among federal or local government agencies, and usage in U.S. infrastructure sectors. Such criteria should also include “consumption patterns” such as how frequently packages are updated, the last time packages were downloaded, and the number of downloads of particular open source dependencies.
Congress should establish a process for funding OSS components that are determined to be both critical and in need of support, as well as improvements to the general ecosystem. Such funding could include:
The agency administering funding should publish clear criteria for the basis under which funding is awarded, and applicants should demonstrate their conformance with these criteria in order to be considered for grants. The results of the critical OSS catalog could also be used to better inform which types of projects and issues are prioritized in the funding and grantmaking process.
One way to accomplish these two recommendations is for Congress to create a Center for Open Source Software Infrastructure and Security, which could be included in the upcoming FY 2022 National Defense Authorization Act (NDAA).
As outlined in the bipartisan Cyberspace Solarium Commission Report<fn-sp>24<fn-sp>, one place to house such a Center would be under the Department of Homeland Security (DHS) Science and Technology Directorate’s (S&T) Homeland Security Advanced Research Projects Agency (HSARPA).
The Center could build on the agency’s work in promoting OSS through the Homeland Open Security Technology (HOST) program<fn-sp>25<fn-sp> and its existing grantmaking capacity, and could attract top talent from the cybersecurity sector to focus resources on better improving OSS infrastructure.
Another potential agency that could house the Center is the Cybersecurity and Infrastructure Security Agency (CISA), as its primary mission is to enhance the security, resiliency, and reliability of the nation's cybersecurity and communications infrastructure.
Establishment and funding for this Center could be added as an amendment to the FY 2022 NDAA, stating clearly as a mandate in the statutory text the two recommended goals outlined above.
Mechanisms for public and philanthropic funding of critical OSS are already in place. The above two recommendations would build on CISA’s recent decision to invest in the open source election auditing software tool Arlo.<fn-sp>26<fn-sp> The European Commission’s FOSSA (in 2014) and FOSSA 2 programs (in 2020) also funded both an inventory of critical OSS infrastructure<fn-sp>27<fn-sp> and a bug bounty program that successfully fixed dozens of critical or high OSS vulnerabilities.<fn-sp>28<fn-sp> Moreover, the Ford Foundation and Sloan Foundation’s Critical Digital Infrastructure Research Fund<fn-sp>29<fn-sp> and the Chan Zuckerberg Initiative’s Essential Open Source Software for Science have supported open source software maintenance and research through a grant program.<fn-sp>30<fn-sp> A Center for Open Source Software Infrastructure and Security would build on such initiatives, but with greater scale and impact.
Public funding of open source has a track record of significant return on investment. Much of the technologies underpinning the Internet, including the widely-used open source Apache Web Server, were enabled only by an initial investment by NSF into the development of NCSA HTTPd decades ago.<fn-sp>31<fn-sp> Additionally, the investment by the World Bank’s Global Facility for Disaster Reduction and Recovery (GFDRR) and its partners in the open source geospatial project GeoNode was conservatively estimated to give a 200% return on investment, in addition to creating a “thriving, mutually beneficial ecosystem” of individuals, government agencies, and private entities.<fn-sp>32<fn-sp> Moreover, public support of OSS has been shown to lead to substantial increases in jobs in the IT sector.<fn-sp>33<fn-sp>
These recommendations have broad support across the aisle. These recommendations directly follow from the bipartisan Cyberspace Solarium Commission Report. Moreover, similar proposals for public funding of OSS have also been included in a 2020 Brookings Institution article<fn-sp>34<fn-sp> and a March 2021 Atlantic Council report calling for a federal “open-source security evangelism and support office.”<fn-sp>35<fn-sp>
Securing and strengthening software supply chains is a national security and economic priority. The United States must prioritize greater open source security by cataloguing and funding the ongoing maintenance of critical open source projects. By establishing a Center for Open Source Software Infrastructure and Security in the FY 2022 NDAA, Congress has an opportunity to strengthen our digital infrastructure, prevent future cyberattacks, and safeguard all American citizens.